FirmwareDroid: Security Analysis of Android Firmware
The Android Open Source Project (AOSP) is probably the most used and customized operating system for smartphones and IoT devices worldwide. Its market share and high adaptability makes Android an interesting operating system for many developers.
Danger in the jungle of the apps from 3rd party developers
Nowadays, we use Android firmware in smartphones, TVs, smartwatches, cars, and other devices by various vendors and manufacturers. The sheer amount of customized Android firmware and devices makes it hard for security analysts to detect potentially harmful applications. Another fact is that many vendors include apps from 3rd party developers. Such bloatware usually has more privileges than standard apps and cannot be removed by the user without rooting the device. In recent years several cases were reported where 3rd party developers could include malicious apps into the Android built chain. Media reports claim that pre-installed malware like Chamois and Triade we able to infect several million devices. Such cases demonstrate the need for better strategies for analyzing Android firmware.
Detection of vulnerabilities and potential harmful Apps
In our study, we analyze the Android firmware eco-system in various ways. We collected a dataset with several thousand Android firmware archives and show that several terabytes of firmware data are waiting on the web to be analyzed. We develop a web service called FirmwareDroid for analyzing Android firmware archives and pre-installed apps and create a dataset of firmware samples. Focusing on Android apps, we automated the process of extracting and scanning pre-installed apps with state of the art open-source tools. We demonstrate on real data that pre-installed apps are, in fact, a a threat to Android’s users, and we can detect several hundred malware samples using scanners like VirusTotal, AndroGuard, and APKiD. With state of the art tools, we could scan more than 900’000 apps during our research and give unique insights into Android custom ROMs. Moreover, we enhanced FirmwareDroid with fuzzy hashing algorithms and used them to detect similarities between binaries.
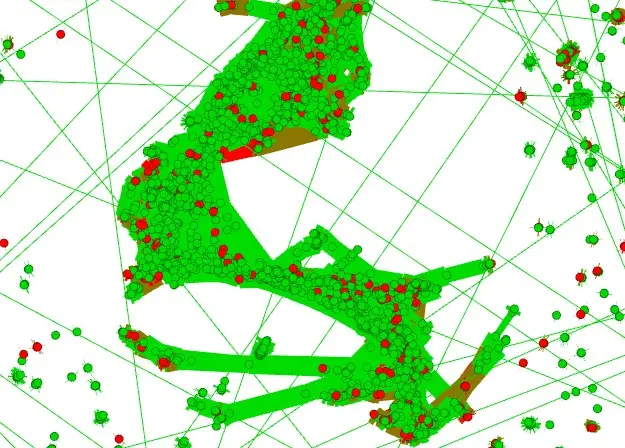
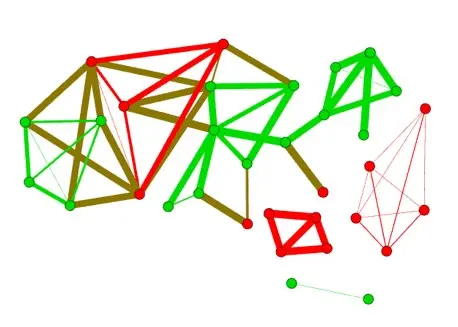
Malware detection with Similarity Analysis
We used fuzzy hashing algorithms to detect similarities between different binaries. A custom fuzzy hashing cluster algorithm was developed to measure code similarity between apps and to detect previously unknown malware. Such fuzzy hash clusters can also be represented as a graph, where each node represents an app and each edge represents the similarity between two apps. The colors in the graph then represent whether an app is classified as harmful (in red) or harmless (in green).
About the author of the thesis
With his master's thesis "FirmwareDroid: Security Analysis often the Android Firmware EcoSystem", Thomas Sutter earned his Master of Science in Engineering (MSE) degree. He was supervised at the Institute for Applied Information Technology. After completing his Master's thesis, he continues to work on the development of FirmwareDroid.
Supervisor: Prof. Dr. Bernhard Tellenbach (former)